AWS Identity Center (SSO) ClickOps
This guide provides an overview of setting up AWS Identity Center (SSO) with ClickOps, detailing prerequisites and supported external identity providers. It explains how to integrate AWS SSO with providers like Azure AD, JumpCloud, Okta, and Google Workspace, including specific steps for configuring each.
How it Works
AWS Single Sign-On (AWS SSO) is a service that simplifies access management for AWS accounts and applications. It enables users to sign in to AWS once and access multiple AWS accounts and applications without the need to re-enter credentials. To use it with an identity provider (IdP) for AWS SSO, administrators typically need to configure the integration within the AWS Management Console. This involves setting up a new AWS SSO instance, connecting it to the IdP, and specifying the users or groups that should have access to AWS resources. AWS SSO provides logging and auditing capabilities, allowing organizations to track user access to AWS resources and monitor security-related events.
1 SAML-Based Authentication
The integration between the IdP and AWS SSO relies on the Security Assertion Markup Language (SAML) for authentication and authorization. SAML enables the exchange of authentication and authorization data between your IdP and AWS, allowing users to log in once to their IdP and gain access to AWS resources without additional logins.
2 User Provisioning
AWS SSO can be configured to automatically provision and de-provision user accounts based on changes in the IdP directory. This helps keep user access in sync with changes made in your IdP.
3 AWS SSO Permission Sets
AWS SSO allows administrators to define fine-grained access policies, specifying which AWS accounts and services users from the IdP can access.
4 Multi-Factor Authentication (MFA)
Organizations using an IdP for authentication with AWS SSO can enhance security by enforcing multi-factor authentication (MFA) for added identity verification.
Once configured, users can experience single sign-on when accessing AWS resources. They log in to their IdP account and seamlessly gain access to AWS without needing to provide credentials again.
It's important to note that the specifics of the integration process may be subject to updates or changes, so it's recommended to refer to the official AWS documentation and your IdP's documentation for the most accurate and up-to-date information.
Prerequisites
First, enable the AWS IAM Identity Center (successor to AWS Single Sign-On) service in the core-root account. This is the account where the aws-sso component will be deployed.
- Navigate to the
core-rootaccount in the AWS Web Console - Select your primary region
- Go to AWS IAM Identity Center (successor to AWS Single Sign-On)
- Enable the service
Configure your Identity Provider
These are the instructions for the most common Identity Providers. Alternatives are available, but the steps may vary depending on the provider.
It's important to note that the specifics of the integration process may be subject to updates or changes, so it's recommended to refer to the official AWS documentation and respective IdP documentation for the most accurate and up-to-date information based on your current date.
For providers not included in the following section, please follow the AWS documentation for setting up an IdP integration with AWS. This list includes Azure AD, CyberArk, OneLogin, and Ping Identity.
- Okta
- JumpCloud
- Microsoft Entra ID
- GSuite and Other External IdPs
Okta is a common business suite that has an active director to manage users and permissions. We can utilize this to login to AWS by leveraging Applications that are used to sign in to things from your Okta Account.
Setup Okta
- Under the Admin Panel go to Applications
- Click Browse App Catalog
- Search for
AWS IAM Identity Centerand click Add Integration - Keep the default settings of App Label ("AWS IAM Identity Center") and Application Visibility
- Go to Sign On and Copy information from the SAML Metadata section, this will be used in AWS SSO.
- Then go to Provisioning and click Configure API Integration
Setup AWS SSO
- Sign into AWS SSO under your management account (
core-root) - Go to the AWS IAM Identity Center (successor to AWS Single Sign-On) application
- Enable IAM Identity Center
- On the left panel click Settings
- Under Identity Source click edit and add an External identity provider
- Copy the information from Okta into the fields
- The Okta App will need to be updated with the Service provider metadata
JumpCloud is a cloud-based directory service that provides secure, frictionless access to AWS resources. It can be used as an identity provider for AWS (Amazon Web Services) through a feature called AWS Single Sign-On (AWS SSO).
Follow the JumpCloud official documentation for setting up JumpCloud with AWS IAM Identity Center:
Integrate with AWS IAM Identity Center
The official AWS documentation for setting up JumpCloud with AWS IAM Identity Center is not accurate. Instead, please refer to the JumpCloud official documentation
Microsoft Entra ID (formerly known as Office 365, Microsoft 365, Azure AD) can be used as an identity provider for AWS (Amazon Web Services) through a feature called AWS Single Sign-On (AWS SSO).
AWS SSO allows organizations to centralize identity management and provide users with seamless access to AWS resources using their existing Microsoft Entra ID credentials.
Setup Microsoft Entra ID
1 Open Microsoft Entra ID Application��
- Microsoft Entra ID
- Azure
Go to Microsoft Entra's Admin Center and search for Entra ID
Go to Microsoft Azure and search for Entra ID

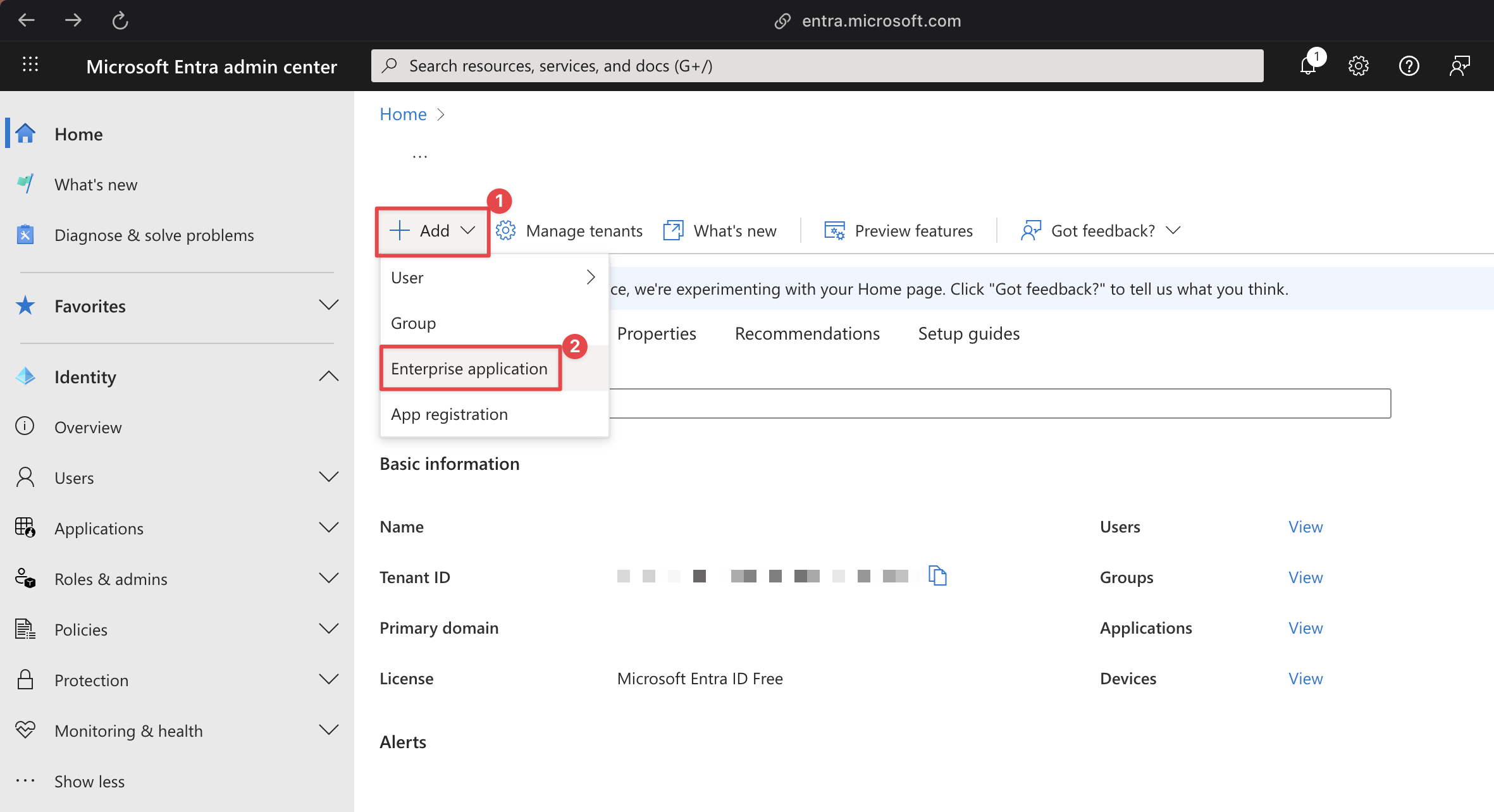
2 Add AWS IAM Identity Center as an Enterprise Application
Click Add then Enterprise Application
Then select AWS IAM Identity Center (successor to AWS Single Sign-On)
- Microsoft Entra ID
- Azure
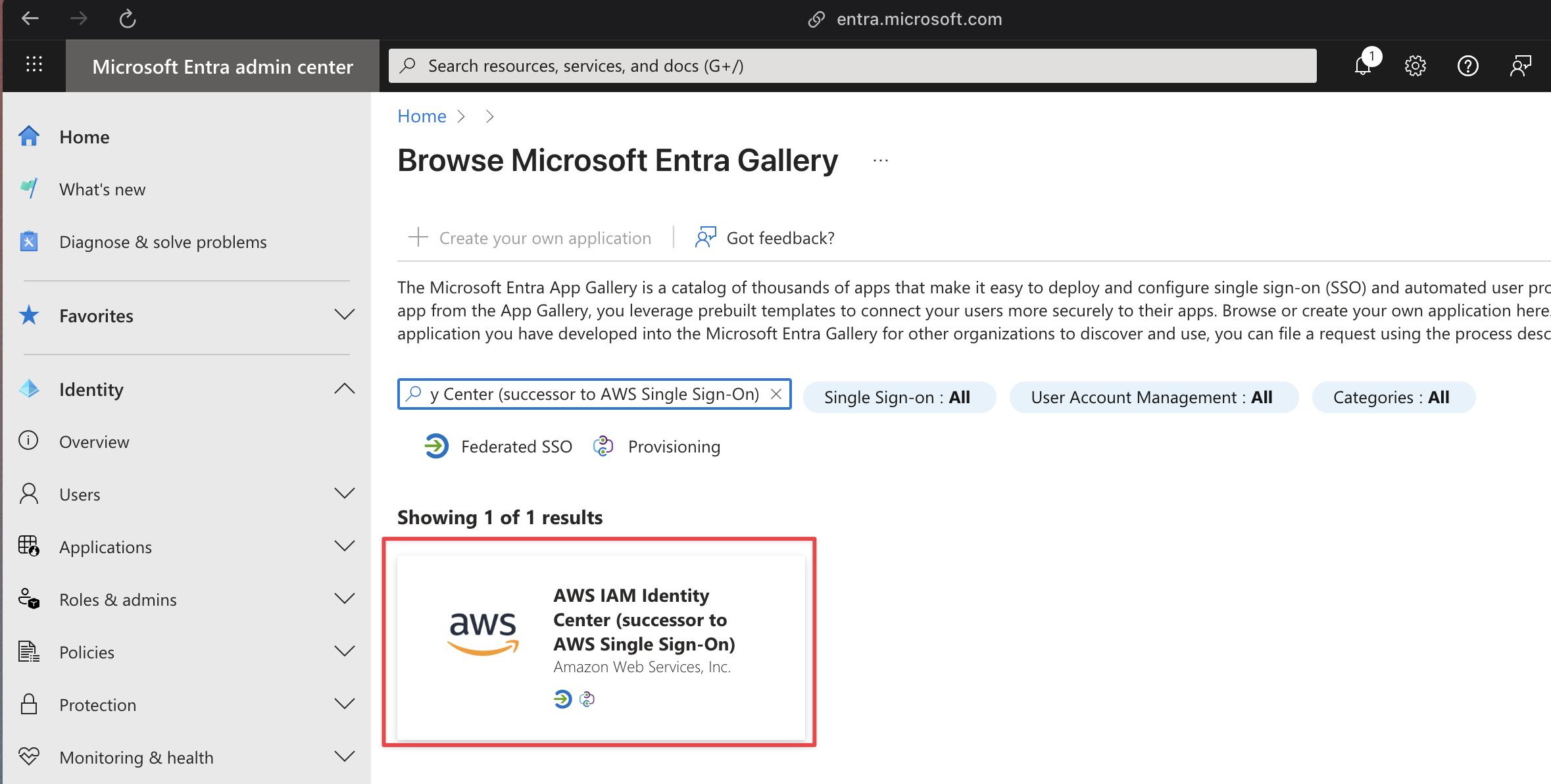
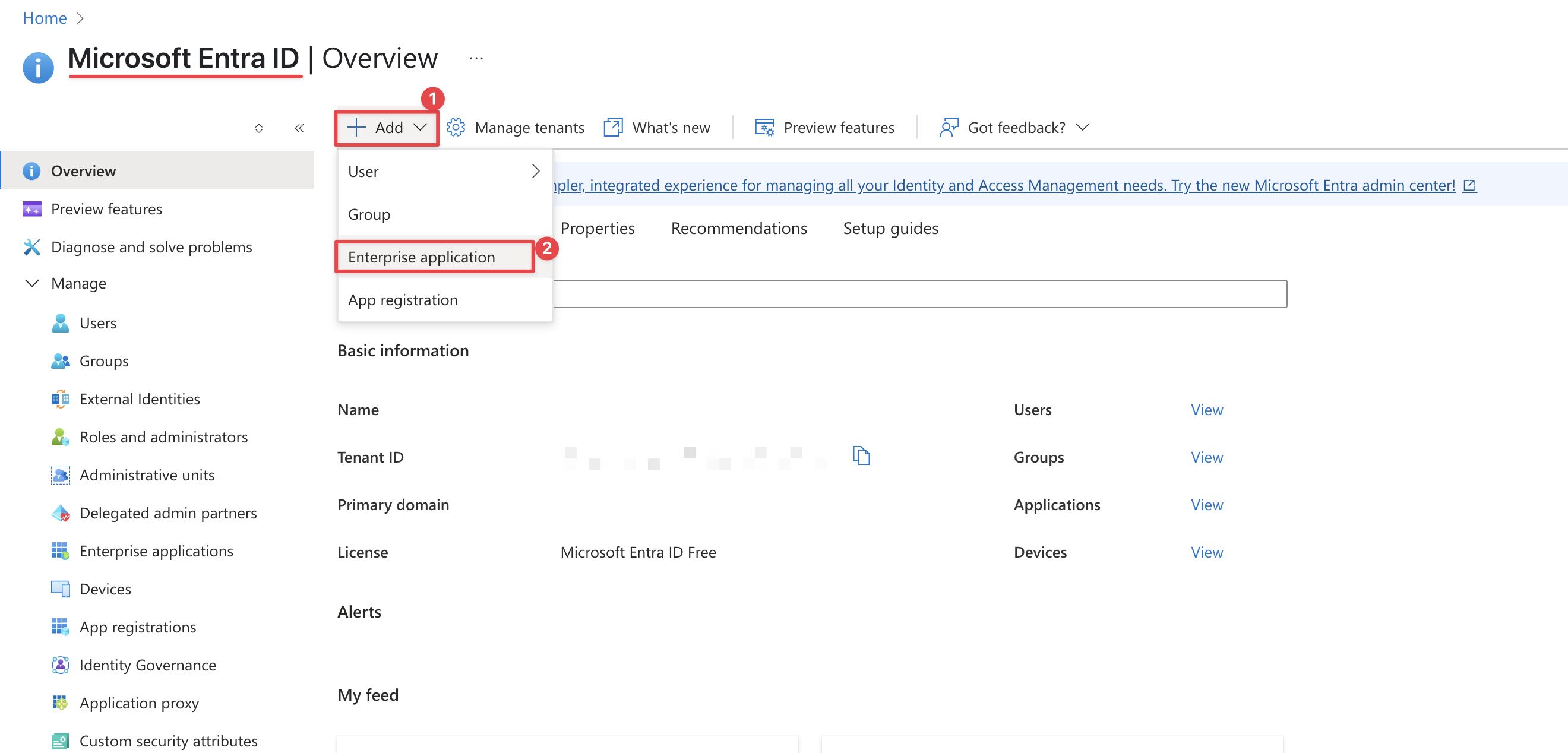
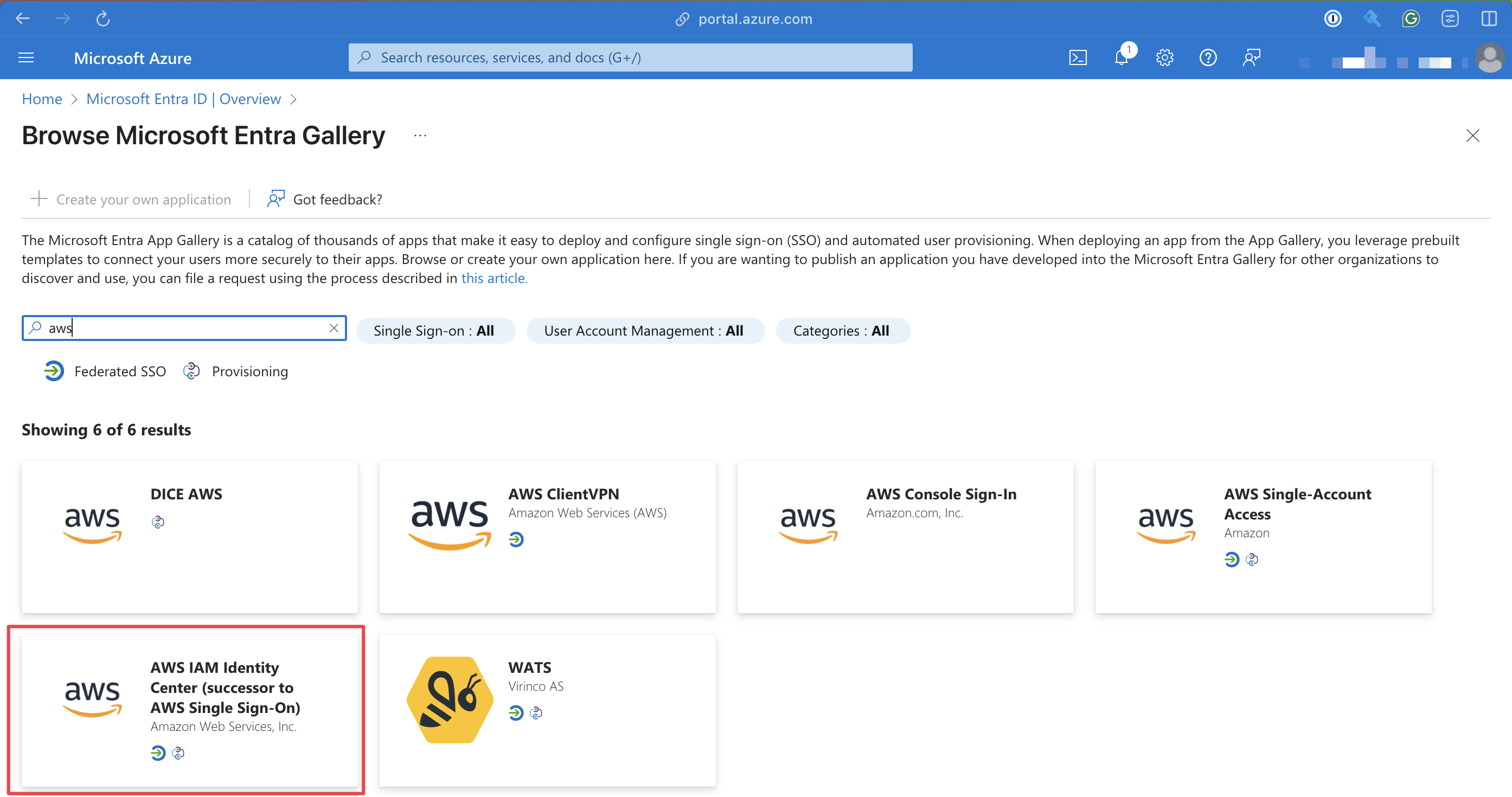
Click Create, default options are fine
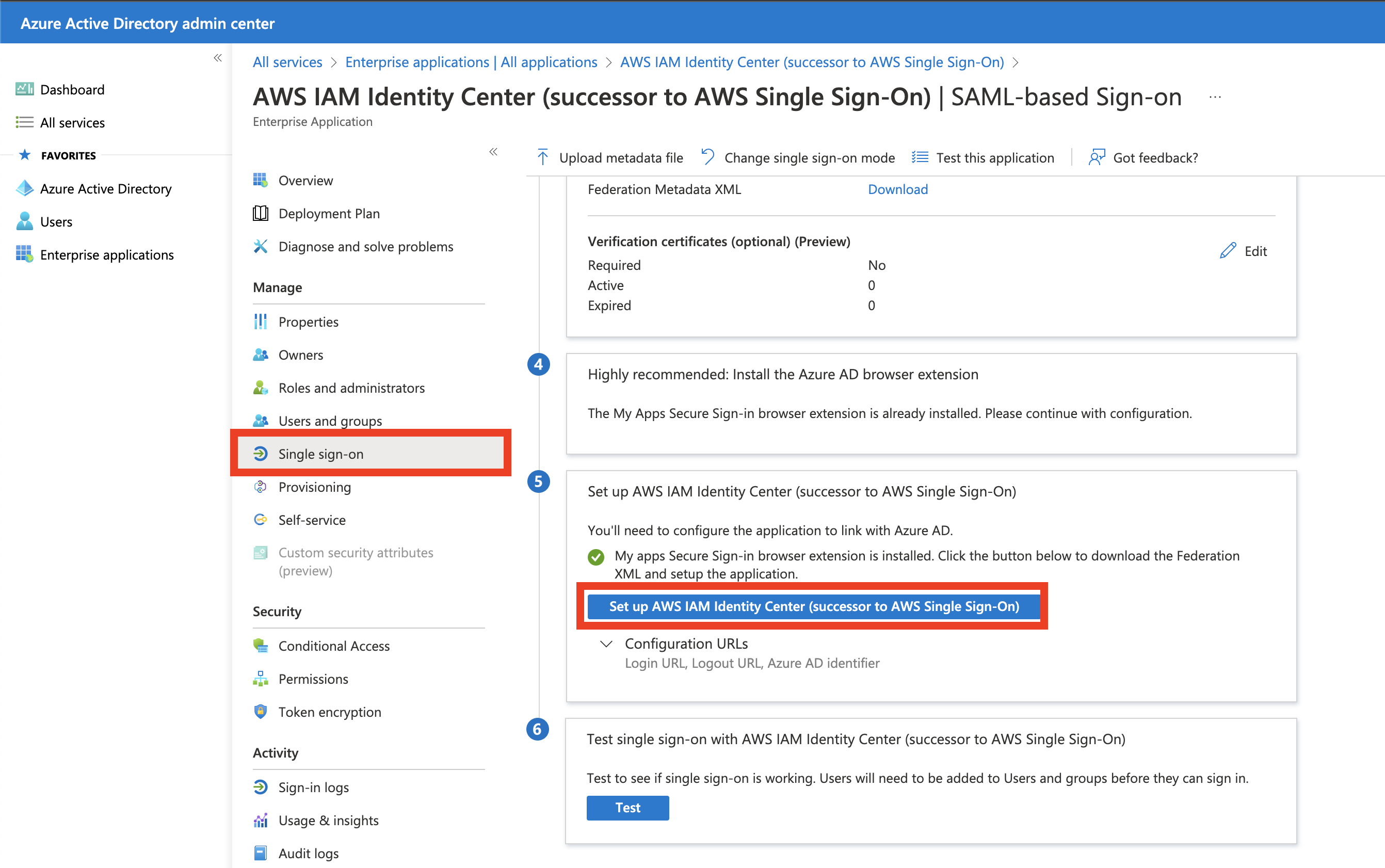
3 Download the Microsoft Entra ID Metadata XML File
On the left panel click Single sign-on, then download the XML SAML metadata file by pressing the button on step 5 Set up AWS IAM Identity Center (successor to AWS Single Sign-On)
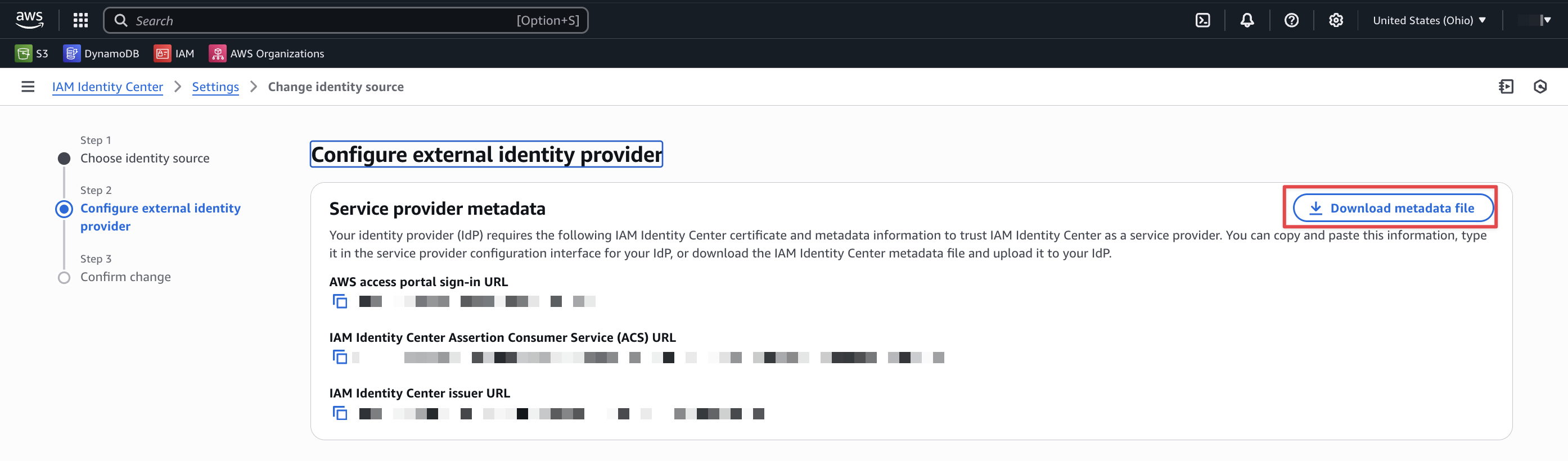
4 Download the AWS IAM Identity Center Metadata XML File
Navigate to the AWS IAM Identity Center (successor to AWS Single Sign-On) application in AWS IAM Identity Center.
Go to Setup/Change Identity Source, click External identity provider from the available identity sources. Click Next.
Download the XML SAML Metadata file by clicking Download metadata file.
5 Upload the Microsoft Entra ID Metadata XML File to AWS
Upload the XML SAML metadata file from Microsoft Entra ID to AWS IAM Identity Center.
6 SAVE
Click Save to save the changes.
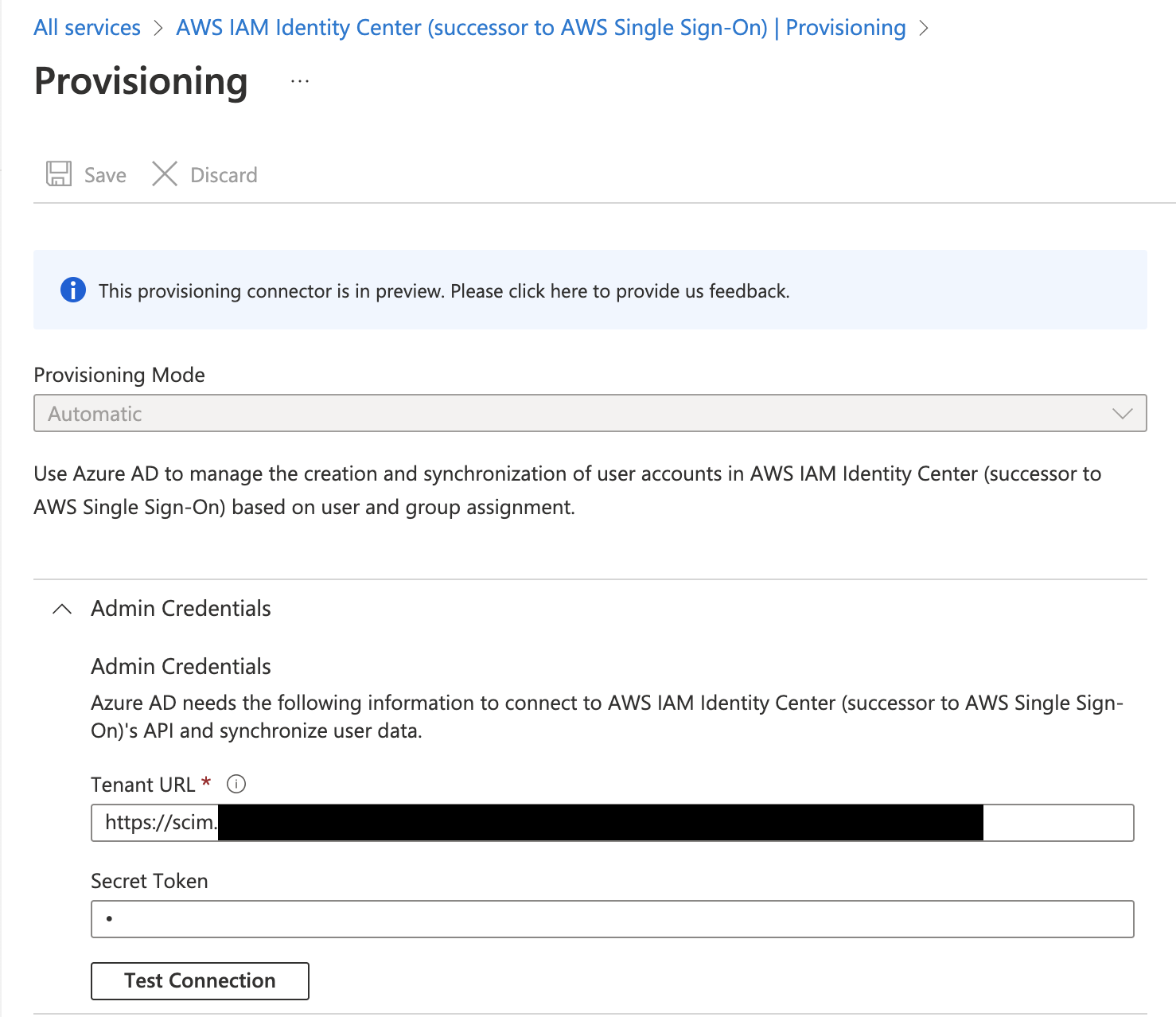
Automatic Provisioning
1 Generate SCIM URL and Secret
In AWS IAM Identity Center, you can set up automatic provisioning by generating a URL and secret

2 Navigate to the new App
Go to Your newly created App for Single Sign On in Microsoft Entra ID, on
the left Panel go to Provisioning.
4 Verify Connection
Click Test Connection to verify the connection.
For non-explicitly supported Identity Providers, such as GSuite, set up the app integration with a custom external identity provider. The steps may be different for each IdP, but the goal is ultimately the same.
GSuite does not automatically sync both Users and Groups with AWS Identity Center without additional configuration! If using GSuite as an IdP, considering deploying the ssosync tool.
Please see our aws-ssosync component for details!
1 Open the Identity account in the AWS Console
2 On the Dashboard page of the IAM Identity Center console, select Choose your identity source
3 In the Settings, choose the Identity source tab, select the Actions dropdown in the top right, and then select Change identity source
4 By default, IAM Identity Center uses its own directory as the IdP. To use another IdP, you have to switch to an external identity provider. Select External identity provider from the available identity sources
5 Configure the custom SAML application with the Service provider metadata generated from your IdP. Follow the next steps from your IdP, and then complete this AWS configuration afterwards
6 Open your chosen IdP
7 Create a new SSO application
8 Download the new app's IdP metadata and use this to complete step 5 above
9 Fill in the Service provider details using the data from IAM Identity Center, and then choose Continue. The mapping for the data is as follows:
For ACS URL, enter the IAM Identity Center Assertion Consumer Service (ACS) URL.
For Entity ID, enter the IAM Identity Center issuer URL.
Leave the Start URL field empty.
For Name ID format, select EMAIL.
10 If required for the IdP, enable the application for all users
11 Finally, define specific Groups to match the given Group names by the aws-sso component (stacks/catalog/aws-sso.yaml). In the default catalog, we define four Groups: DevOps, Developers, BillingAdmin, and Everyone
If set up properly, Users and Groups added to your IdP will automatically populate and update in AWS.
Additional IdP specific setup reference can be found here:
Required Groups
Before deploying the aws-sso component, you must create the following groups in your Identity Provider. These names are case-sensitive and must match exactly:
- Managers — Full access to all accounts
- DevOps — Full access to most accounts (except root)
- Developers — Limited access for development work
- BillingAdmin — Access to billing and cost management
Once these groups are provisioned and synced to AWS Identity Center, you can deploy the aws-sso component.
Deploy Permission Sets
The aws-sso component deploys all Permission Sets and assigns them to the appropriate groups. This includes:
TerraformApplyAccess— Write access for Terraform operationsTerraformPlanAccess— Read-only access for Terraform plan operationsTerraformStateAccess— Access to Terraform state onlyAdministratorAccess— Full AWS administrator accessPowerUserAccess— Power user access without IAM managementReadOnlyAccess— Read-only access to AWS resourcesRootAccess— Organizational root access for privileged operations (see Centralized Root Access)
The aws-sso component is responsible for deploying all Permission Sets and mapping them to the appropriate groups per account. This mapping is configured in stacks/catalog/aws-sso.yaml, where you define which groups receive which Permission Sets for each account type. This is how you assign permissions to users — by adding them to the appropriate IdP group, they automatically receive the corresponding Permission Sets when they access AWS.
Deploy the component using the identity workflow:
The aws-sso component will fail if the required groups (Managers, DevOps, Developers, BillingAdmin) do not exist in AWS Identity Center. Ensure your IdP is configured and groups are synced before deploying.
Next Steps
Centralize root access
Now that Identity Center and Permission Sets are provisioned, configure centralized root access management. This allows secure, auditable root operations on member accounts without maintaining root credentials. Centralize Root Access