Module: vpc-peering-multi-account
Terraform module to create a peering connection between any two VPCs existing in different AWS accounts.
This module supports performing this action from a 3rd account (e.g. a "root" account) by specifying the roles to assume for each member account.
IMPORTANT: AWS allows a multi-account VPC Peering Connection to be deleted from either the requester's or accepter's side.
However, Terraform only allows the VPC Peering Connection to be deleted from the requester's side by removing the corresponding aws_vpc_peering_connection resource from your configuration.
Read more about this on Terraform's documentation portal.
Screenshots
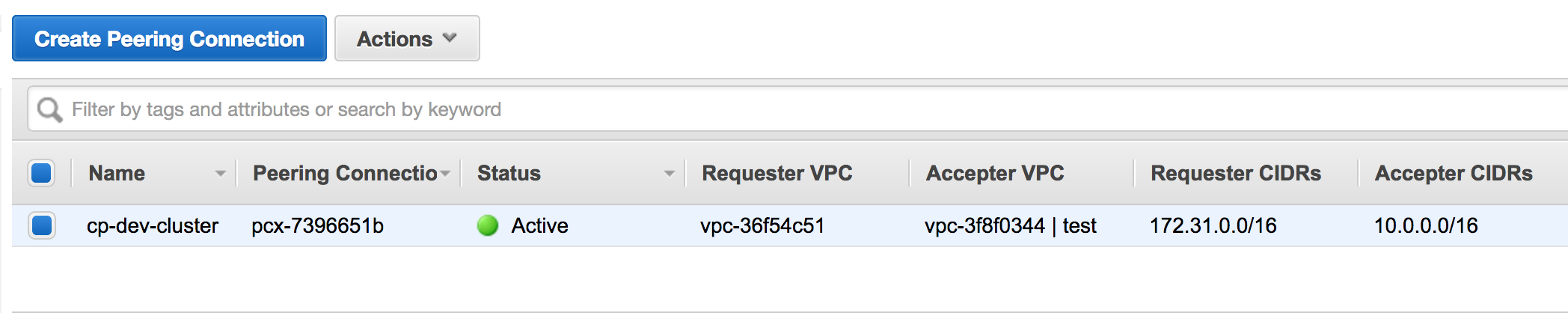 VPC Peering Connection in the AWS Web Console
VPC Peering Connection in the AWS Web Console
Usage
IMPORTANT: Do not pin to master because there may be breaking changes between releases. Instead pin to the release tag (e.g. ?ref=tags/x.y.z) of one of our latest releases.
For a complete example, see examples/complete
provider "aws" {
alias = "requester"
region = "us-west-2"
assume_role {
role_arn = "arn:aws:iam::XXXXXXXX:role/cross-account-vpc-peering-test"
}
}
provider "aws" {
alias = "accepter"
region = "us-east-1"
assume_role {
role_arn = "arn:aws:iam::YYYYYYYY:role/cross-account-vpc-peering-test"
}
}
module "vpc_peering_cross_account" {
source = "cloudposse/vpc-peering-multi-account/aws"
# Cloud Posse recommends pinning every module to a specific version
# version = "x.x.x"
namespace = "eg"
stage = "dev"
name = "cluster"
providers = {
aws.requester = aws.requester
aws.accepter = aws.accepter
}
requester_vpc_id = "vpc-xxxxxxxx"
requester_allow_remote_vpc_dns_resolution = true
accepter_vpc_id = "vpc-yyyyyyyy"
accepter_allow_remote_vpc_dns_resolution = true
}
The arn:aws:iam::XXXXXXXX:role/cross-account-vpc-peering-test requester IAM Role should have the following Trust Policy:
Show Trust Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::XXXXXXXX:root"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
and the following IAM Policy attached to it:
NOTE: the policy specifies the permissions to create (with terraform plan/apply) and delete (with terraform destroy) all the required resources in the requester AWS account
Show IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:CreateRoute",
"ec2:DeleteRoute"
],
"Resource": "arn:aws:ec2:*:XXXXXXXX:route-table/*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:ModifyVpcPeeringConnectionOptions",
"ec2:DescribeSubnets",
"ec2:DescribeVpcAttribute",
"ec2:DescribeRouteTables"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:AcceptVpcPeeringConnection",
"ec2:DeleteVpcPeeringConnection",
"ec2:CreateVpcPeeringConnection",
"ec2:RejectVpcPeeringConnection"
],
"Resource": [
"arn:aws:ec2:*:XXXXXXXX:vpc-peering-connection/*",
"arn:aws:ec2:*:XXXXXXXX:vpc/*"
]
},
{
"Effect": "Allow",
"Action": [
"ec2:DeleteTags",
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:XXXXXXXX:vpc-peering-connection/*"
}
]
}
where XXXXXXXX is the requester AWS account ID.
The arn:aws:iam::YYYYYYYY:role/cross-account-vpc-peering-test accepter IAM Role should have the following Trust Policy:
Show Trust Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::XXXXXXXX:root"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
NOTE: The accepter Trust Policy is the same as the requester Trust Policy since it defines who can assume the IAM Role.
In the requester case, the requester account ID itself is the trusted entity.
For the accepter, the Trust Policy specifies that the requester account ID XXXXXXXX can assume the role in the accepter AWS account YYYYYYYY.
and the following IAM Policy attached to it:
NOTE: the policy specifies the permissions to create (with terraform plan/apply) and delete (with terraform destroy) all the required resources in the accepter AWS account
Show IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:CreateRoute",
"ec2:DeleteRoute"
],
"Resource": "arn:aws:ec2:*:YYYYYYYY:route-table/*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:ModifyVpcPeeringConnectionOptions",
"ec2:DescribeSubnets",
"ec2:DescribeVpcAttribute",
"ec2:DescribeRouteTables"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:AcceptVpcPeeringConnection",
"ec2:DeleteVpcPeeringConnection",
"ec2:CreateVpcPeeringConnection",
"ec2:RejectVpcPeeringConnection"
],
"Resource": [
"arn:aws:ec2:*:YYYYYYYY:vpc-peering-connection/*",
"arn:aws:ec2:*:YYYYYYYY:vpc/*"
]
},
{
"Effect": "Allow",
"Action": [
"ec2:DeleteTags",
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:YYYYYYYY:vpc-peering-connection/*"
}
]
}
where YYYYYYYY is the accepter AWS account ID.
For more information on IAM policies and permissions for VPC peering, see Creating and managing VPC peering connections.
Variables
Required Variables
Optional Variables
accepter_allow_remote_vpc_dns_resolution(bool) optionalAllow accepter VPC to resolve public DNS hostnames to private IP addresses when queried from instances in the requester VPC
Default value:
trueaccepter_enabled(bool) optionalFlag to enable/disable the accepter side of the peering connection
Default value:
trueaccepter_subnet_tags(map(string)) optionalOnly add peer routes to accepter VPC route tables of subnets matching these tags
Default value:
{ }accepter_vpc_id(string) optionalAccepter VPC ID filter
Default value:
""accepter_vpc_tags(map(string)) optionalAccepter VPC Tags filter
Default value:
{ }add_attribute_tag(bool) optionalIf
truewill add additional attribute tag to the requester and accceptor resourcesDefault value:
trueauto_accept(bool) optionalAutomatically accept the peering
Default value:
trueaws_route_create_timeout(string) optionalTime to wait for AWS route creation specifed as a Go Duration, e.g.
2mDefault value:
"5m"aws_route_delete_timeout(string) optionalTime to wait for AWS route deletion specifed as a Go Duration, e.g.
5mDefault value:
"5m"requester_allow_remote_vpc_dns_resolution(bool) optionalAllow requester VPC to resolve public DNS hostnames to private IP addresses when queried from instances in the accepter VPC
Default value:
truerequester_subnet_tags(map(string)) optionalOnly add peer routes to requester VPC route tables of subnets matching these tags
Default value:
{ }requester_vpc_id(string) optionalRequester VPC ID filter
Default value:
""requester_vpc_tags(map(string)) optionalRequester VPC Tags filter
Default value:
{ }
Context Variables
The following variables are defined in the context.tf file of this module and part of the terraform-null-label pattern.
context.tf file of this module and part of the terraform-null-label pattern.additional_tag_map(map(string)) optionalAdditional key-value pairs to add to each map in
tags_as_list_of_maps. Not added totagsorid.
This is for some rare cases where resources want additional configuration of tags
and therefore take a list of maps with tag key, value, and additional configuration.Required: No
Default value:
{ }attributes(list(string)) optionalID element. Additional attributes (e.g.
workersorcluster) to add toid,
in the order they appear in the list. New attributes are appended to the
end of the list. The elements of the list are joined by thedelimiter
and treated as a single ID element.Required: No
Default value:
[ ]context(any) optionalSingle object for setting entire context at once.
See description of individual variables for details.
Leave string and numeric variables asnullto use default value.
Individual variable settings (non-null) override settings in context object,
except for attributes, tags, and additional_tag_map, which are merged.Required: No
Default value:
{
"additional_tag_map": {},
"attributes": [],
"delimiter": null,
"descriptor_formats": {},
"enabled": true,
"environment": null,
"id_length_limit": null,
"label_key_case": null,
"label_order": [],
"label_value_case": null,
"labels_as_tags": [
"unset"
],
"name": null,
"namespace": null,
"regex_replace_chars": null,
"stage": null,
"tags": {},
"tenant": null
}delimiter(string) optionalDelimiter to be used between ID elements.
Defaults to-(hyphen). Set to""to use no delimiter at all.Required: No
Default value:
nulldescriptor_formats(any) optionalDescribe additional descriptors to be output in the
descriptorsoutput map.
Map of maps. Keys are names of descriptors. Values are maps of the form
\{<br/> format = string<br/> labels = list(string)<br/> \}
(Type isanyso the map values can later be enhanced to provide additional options.)
formatis a Terraform format string to be passed to theformat()function.
labelsis a list of labels, in order, to pass toformat()function.
Label values will be normalized before being passed toformat()so they will be
identical to how they appear inid.
Default is{}(descriptorsoutput will be empty).Required: No
Default value:
{ }enabled(bool) optionalSet to false to prevent the module from creating any resources
Required: NoDefault value:
nullenvironment(string) optionalID element. Usually used for region e.g. 'uw2', 'us-west-2', OR role 'prod', 'staging', 'dev', 'UAT'
Required: NoDefault value:
nullid_length_limit(number) optionalLimit
idto this many characters (minimum 6).
Set to0for unlimited length.
Set tonullfor keep the existing setting, which defaults to0.
Does not affectid_full.Required: No
Default value:
nulllabel_key_case(string) optionalControls the letter case of the
tagskeys (label names) for tags generated by this module.
Does not affect keys of tags passed in via thetagsinput.
Possible values:lower,title,upper.
Default value:title.Required: No
Default value:
nulllabel_order(list(string)) optionalThe order in which the labels (ID elements) appear in the
id.
Defaults to ["namespace", "environment", "stage", "name", "attributes"].
You can omit any of the 6 labels ("tenant" is the 6th), but at least one must be present.Required: No
Default value:
nulllabel_value_case(string) optionalControls the letter case of ID elements (labels) as included in
id,
set as tag values, and output by this module individually.
Does not affect values of tags passed in via thetagsinput.
Possible values:lower,title,upperandnone(no transformation).
Set this totitleand setdelimiterto""to yield Pascal Case IDs.
Default value:lower.Required: No
Default value:
nulllabels_as_tags(set(string)) optionalSet of labels (ID elements) to include as tags in the
tagsoutput.
Default is to include all labels.
Tags with empty values will not be included in thetagsoutput.
Set to[]to suppress all generated tags.
Notes:
The value of thenametag, if included, will be theid, not thename.
Unlike othernull-labelinputs, the initial setting oflabels_as_tagscannot be
changed in later chained modules. Attempts to change it will be silently ignored.Required: No
Default value:
[
"default"
]name(string) optionalID element. Usually the component or solution name, e.g. 'app' or 'jenkins'.
This is the only ID element not also included as atag.
The "name" tag is set to the fullidstring. There is no tag with the value of thenameinput.Required: No
Default value:
nullnamespace(string) optionalID element. Usually an abbreviation of your organization name, e.g. 'eg' or 'cp', to help ensure generated IDs are globally unique
Required: NoDefault value:
nullregex_replace_chars(string) optionalTerraform regular expression (regex) string.
Characters matching the regex will be removed from the ID elements.
If not set,"/[^a-zA-Z0-9-]/"is used to remove all characters other than hyphens, letters and digits.Required: No
Default value:
nullstage(string) optionalID element. Usually used to indicate role, e.g. 'prod', 'staging', 'source', 'build', 'test', 'deploy', 'release'
Required: NoDefault value:
nulltags(map(string)) optionalAdditional tags (e.g.
{'BusinessUnit': 'XYZ'}).
Neither the tag keys nor the tag values will be modified by this module.Required: No
Default value:
{ }tenant(string) optionalID element (Rarely used, not included by default). A customer identifier, indicating who this instance of a resource is for
Required: NoDefault value:
null
Outputs
accepter_accept_statusAccepter VPC peering connection request status
accepter_connection_idAccepter VPC peering connection ID
accepter_subnet_route_table_mapMap of accepter VPC subnet IDs to route table IDs
requester_accept_statusRequester VPC peering connection request status
requester_connection_idRequester VPC peering connection ID
Dependencies
Requirements
terraform, version:>= 1.3aws, version:>= 2.0
Providers
aws, version:>= 2.0aws, version:>= 2.0
Modules
| Name | Version | Source | Description |
|---|---|---|---|
accepter | 0.25.0 | cloudposse/label/null | n/a |
requester | 0.25.0 | cloudposse/label/null | n/a |
this | 0.25.0 | cloudposse/label/null | n/a |
Resources
The following resources are used by this module:
aws_route.accepter(resource)aws_route.accepter_ipv6(resource)aws_route.requester(resource)aws_route.requester_ipv6(resource)aws_vpc_peering_connection.requester(resource)aws_vpc_peering_connection_accepter.accepter(resource)aws_vpc_peering_connection_options.accepter(resource)aws_vpc_peering_connection_options.requester(resource)
Data Sources
The following data sources are used by this module:
aws_caller_identity.accepter(data source)aws_caller_identity.requester(data source)aws_region.accepter(data source)aws_region.requester(data source)aws_route_table.requester(data source)aws_route_tables.accepter(data source)aws_route_tables.default_rts(data source)aws_subnet.accepter(data source)aws_subnet.requester(data source)aws_subnets.accepter(data source)aws_subnets.requester(data source)aws_vpc.accepter(data source)aws_vpc.requester(data source)